Merhaba
USA Army Research Lab tarafından geliştirilen ve github üzerinden opensource olarak ulaşılabilen Dshell, son zamanlarda ilgimi çeken güzel bir network forensic aracı. Bu blog yazısında kurulum ve basit düzeyde kullanımı hakkında bilgilerin paylaşılacağı Dshell son derece geliştirilebilir ve plugin yazılabilir ortam sağlamaktadır.
Kurulum
Kurulum öncesi gerekli olan bağımlılıkların kurulumu gerçekleştirilmelidir.
sudo apt-get install python-crypto python-dpkt python-ipy python-pypcap sudo pip install pygeoip
Ardından Dshell github üzerinden clonlanır ve kurulum tamamlanır.
git clone https://github.com/USArmyResearchLab/Dshell.git bash install-ubuntu.sh
Cryptolocker Varyantı Network Paketi Analizi
Dshell aracının imkanlarını anlayabilmek adına CryptoLocker varyantı olan bir .exe ‘nin trafiğini analiz etmeye karar verdim. Network trafiği üzerinde dshell ile analiz gerçekleştirilen sample’ın hash değeri ve virustotal raporu aşağıdadır.
Malware Hash = 64c6764f569a663407552b98b5458757145b97e0513805ff9acd65352f7596c1
Virus Total Raporu = https://www.virustotal.com/en/file/64c6764f569a663407552b98b5458757145b97e0513805ff9acd65352f7596c1/analysis/
Malwr Raporu = https://malwr.com/analysis/YjgwYmMwYTYzZWI5NGJlZTk1MmMwODNjYTM1MTVjODQ/
Eğer pcap dosyasını indirmek isterseniz = http://www.malware-traffic-analysis.net/2014/04/14/2014-04-14-Magnitude-EK-traffic.pcap
Dshell Komutları
Dshell’in default olarak kendisinde bulunan decode modülleri aşağıdaki gibidir.
mince@rootlab:~/pentest/Dshell Dshell> decode -l module name author desc ---------------------------------------- ------------------------------ ---------- --- - -------------------------------------------------- decoders.dns.dns dns bg/twp TCP extract and summarize DNS queries/responses (defaults: A,AAAA,CNAME,PTR records) decoders.dns.dns-asn dns-asn bg TCP identify AS of DNS A/AAAA record responses decoders.dns.dns-cc dns-cc bg TCP identify country code of DNS A/AAAA record responses decoders.dns.innuendo-dns innuendo-dns primalsec TCP proof-of-concept detector for INNUENDO DNS channel decoders.dns.reservedips reservedips bg TCP identify DNS resolutions that fall into reserved ip space decoders.filter.country country twp TCP + filter connections on geolocation (country code) decoders.filter.snort snort twp RAW + filter packets by snort rule decoders.filter.track track twp TCP + tracked activity recorder decoders.flows.large-flows large-flows bg TCP display netflows that have at least 1MB transferred decoders.flows.long-flows long-flows bg TCP display netflows that have a duration of at least 5mins decoders.flows.netflow netflow bg TCP generate netflow information from pcap decoders.http.httpdump httpdump amm TCP Dump useful information about HTTP sessions decoders.http.rip-http rip-http bg/twp TCP rip files from HTTP traffic decoders.http.web web bg,twp TCP Improved version of web that tracks server response decoders.misc.followstream followstream amm TCP Generates color-coded Screen/HTML output similar to Wireshark Follow Stream decoders.misc.merge merge bg/twp RAW + dump all packets to single file decoders.misc.synrst synrst bg RAW detect failed attempts to connect (SYN followed by a RST/ACK) decoders.misc.writer writer twp RAW pcap/session writer decoders.misc.xor xor twp TCP + XOR an entire stream with a given single byte key decoders.protocol.ether ether twp RAW raw ethernet capture decoder decoders.protocol.ip ip twp RAW IPv4/IPv6 decoder decoders.protocol.protocol protocol bg RAW Identifies non-standard protocols (not tcp, udp or icmp) decoders.templates.PacketDecoder unnamed xx RAW decoders.templates.SessionDecoder unnamed xx TCP
DNS paketleri
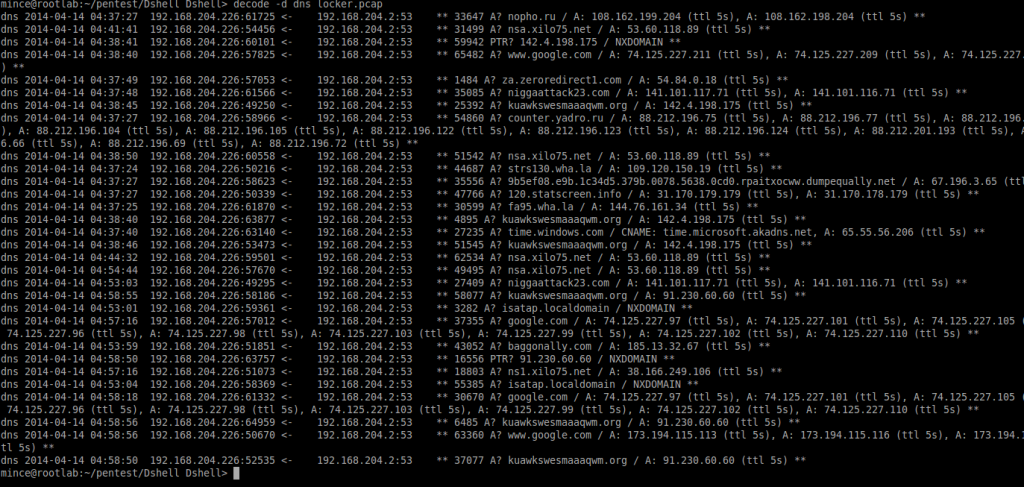
İlk aşamda malware çalıştığı anda oluşturduğu DNS sorgularını görmek basit bir komutla mümkündür. Bir önceki kısımda listelediğimiz dshell decoder listesinden dns decoderını seçerek -d parametresine veriyoruz.
Dshell> decode -d dns locker.pcap
Bu listeye bakarak C2 sunucularının listesi rahatlıkla çıkartılabilmektedir.
Dosya boyutuna göre listeme
Dsniff’in large-flows isimli modülü en az 1 MB transferin gerçekleştirildiği aktiviteleri listelemektedir.
mince@rootlab:~/pentest/Dshell Dshell> decode -d large-flows locker.pcap 2014-04-14 01:37:32.777635 192.168.204.226 -> 67.196.3.65 (None -> None) TCP 49194 80 1 131 283 188622 0.5063s 2014-04-14 01:37:25.460347 192.168.204.226 -> 109.120.150.19 (None -> None) TCP 49178 80 8 103 3347 143248 18.2243s 2014-04-14 01:37:24.765214 192.168.204.226 -> 109.120.150.19 (None -> None) TCP 49177 80 9 90 3839 121280 19.3525s 2014-04-14 01:38:11.627113 192.168.204.226 -> 67.196.3.65 (None -> None) TCP 49216 80 1 528 283 769742 1.0930s 2014-04-14 01:38:13.533634 192.168.204.226 -> 67.196.3.65 (None -> None) TCP 49218 80 1 186 283 270542 0.5369s 2014-04-14 01:38:14.911637 192.168.204.226 -> 67.196.3.65 (None -> None) TCP 49219 80 1 74 283 106550 0.3485s 2014-04-14 01:38:16.471322 192.168.204.226 -> 67.196.3.65 (None -> None) TCP 49220 80 1 274 283 398271 0.7096s 2014-04-14 01:39:10.850235 192.168.204.226 -> 91.220.131.58 (None -> None) TCP 49246 80 1 653 55 774247 10.5614s 2014-04-14 01:37:46.211514 192.168.204.226 -> 87.224.219.174 (None -> None) TCP 49196 80 1 642 56 769893 97.4168s 2014-04-14 01:37:50.235760 192.168.204.226 -> 89.215.196.42 (None -> None) TCP 49201 80 1 675 55 847920 93.3926s
Bu tür trafikler genellikle dropperin hedef sistemde çalışmasının ardından asıl zararlı yazılımın indiriliyor olması ile ilgilidir. Bu durumda da indirlen zararlı yazılımı tespit etmek adına web taleplerini listelememiz gerekecektir.
mince@rootlab:~/pentest/Dshell Dshell> decode -d web locker.pcap web 2014-04-14 04:37:21 192.168.204.226:49171 -> 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/ HTTP/1.1 // 200 OK 2014-04-14 01:04:33 ** web 2014-04-14 04:37:21 192.168.204.226:49171 -> 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/media/system/js/mootools.js HTTP/1.1 // 200 OK 2012-01-17 11:01:01 ** web 2014-04-14 04:37:21 192.168.204.226:49171 -> 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/templates/rhuk_milkyway/css/t[truncated] HTTP/1.1 // 200 OK 2012-01-13 12:18:45 ** web 2014-04-14 04:37:21 192.168.204.226:49171 -> 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/templates/rhuk_milkyway/image[truncated] HTTP/1.1 // 200 OK 2012-01-13 12:18:48 ** web 2014-04-14 04:37:21 192.168.204.226:49171 -> 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/templates/rhuk_milkyway/image[truncated] HTTP/1.1 // 200 OK 2012-01-13 12:18:53 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/index.php HTTP/1.1 // 200 OK 2014-04-14 01:37:25 ** web 2014-04-14 04:37:25 192.168.204.226:49178 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/engine/classes/js/jquer[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/engine/classes/js/jquer[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:21 192.168.204.226:49171 -> 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/templates/rhuk_milkyway/image[truncated] HTTP/1.1 // 200 OK 2012-01-13 12:19:24 ** web 2014-04-14 04:37:25 192.168.204.226:49178 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/engine/classes/js/dle_j[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/c[truncated] HTTP/1.1 // 200 OK 2014-01-11 11:35:10 ** web 2014-04-14 04:37:21 192.168.204.226:49171 -> 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/templates/rhuk_milkyway/image[truncated] HTTP/1.1 // 200 OK 2012-01-13 12:18:52 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/c[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/j[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:25 192.168.204.226:49178 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/c[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/j[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:25 192.168.204.226:49178 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:25 192.168.204.226:49178 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:24 192.168.204.226:49177 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49180 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49181 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 404 Not Found 2014-04-14 01:37:28 ** web 2014-04-14 04:37:27 192.168.204.226:49182 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49192 <- 67.196.3.65:80 ** GET 9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally.net/ HTTP/1.1 // 200 OK 2014-04-14 01:37:15 ** web 2014-04-14 04:37:25 192.168.204.226:49178 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:21 192.168.204.226:49171 <- 95.141.36.68:80 ** GET www.uiltrasporticalabria.it/templates/rhuk_milkyway/image[truncated] HTTP/1.1 // 200 OK 2012-01-13 12:19:24 ** web 2014-04-14 04:37:27 192.168.204.226:49180 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49181 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49182 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:25 192.168.204.226:49178 -> 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:30 192.168.204.226:49193 <- 67.196.3.65:80 ** GET 9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally.net/0e9c6b8d847dde5934bf356ff1639[truncated] HTTP/1.1 // 200 OK web 2014-04-14 04:37:32 192.168.204.226:49194 <- 67.196.3.65:80 ** GET 67.196.3.65/?bdef493dd79d22954b8eed25fd94[truncated] HTTP/1.1 // 200 OK 2014-04-14 01:37:19 ** web 2014-04-14 04:37:40 192.168.204.226:49195 <- 67.196.3.65:80 ** GET 67.196.3.65/?f374ddbff953c15fbc2664903037[truncated] HTTP/1.1 // 200 OK 2014-04-14 01:37:27 ** web 2014-04-14 04:37:25 192.168.204.226:49179 <- 144.76.161.34:80 ** GET fa95.wha.la/zxzzzzzdddff/?id=ts HTTP/1.1 // 302 Found -> http://9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally.net/ 2014-04-14 01:37:26 ** web 2014-04-14 04:37:27 192.168.204.226:49183 <- 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49180 <- 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49182 <- 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:27 192.168.204.226:49181 <- 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:25 192.168.204.226:49178 <- 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-10 05:07:58 ** web 2014-04-14 04:37:24 192.168.204.226:49177 <- 109.120.150.19:80 ** GET strs130.wha.la/zismo/templates/glamurgirls/i[truncated] HTTP/1.1 // 200 OK 2014-01-11 18:18:38 ** web 2014-04-14 04:37:49 192.168.204.226:49200 <- 54.84.0.18:80 ** GET za.zeroredirect1.com/zcvisitor/633b2fa4-c375-11e3-[truncated] HTTP/1.1 // 200 OK 2014-04-14 01:37:49 ** web 2014-04-14 04:37:48 192.168.204.226:49198 <- 141.101.117.71:80 ** POST niggaattack23.com/2a628t577por5c HTTP/1.1 // 522 Origin Connection Time-out 2014-04-14 web 2014-04-14 04:38:16 192.168.204.226:49220 <- 67.196.3.65:80 ** GET 67.196.3.65/?ff8e988281414d46f1dd1a29cc5e[truncated] HTTP/1.1 // 200 OK 2014-04-14 01:38:03 ** web 2014-04-14 04:38:40 192.168.204.226:49229 <- 74.125.227.211:80 ** GET www.google.com/ HTTP/1.1 // ** web 2014-04-14 04:38:46 192.168.204.226:49232 <- 74.125.227.211:80 ** GET www.google.com/ HTTP/1.1 // ** web 2014-04-14 04:38:06 192.168.204.226:49202 <- 141.101.117.71:80 ** POST niggaattack23.com/psfxwfddej1roh HTTP/1.1 // 200 OK 1970-01-01 02:46:40 ** web 2014-04-14 04:38:45 192.168.204.226:49231 <- 142.4.198.175:80 ** POST kuawkswesmaaaqwm.org/ HTTP/1.1 // 404 Not Found 2014-04-14 01:39:28 ** web 2014-04-14 04:38:48 192.168.204.226:49234 -> 141.101.117.71:80 ** POST niggaattack23.com/68qmqzyt1326xx8 HTTP/1.1 // 522 Origin Connection Time-out 2014-04-14 01:39:03 web 2014-04-14 04:39:10 192.168.204.226:49246 <- 91.220.131.58:80 ** GET 91.220.131.58/mod1/5minut1.exe HTTP/1.0 // 200 OK 2014-04-14 01:25:46 ** web 2014-04-14 04:37:46 192.168.204.226:49196 <- 87.224.219.174:80 ** GET 87.224.219.174/mod1/5minut1.exe HTTP/1.0 // ** web 2014-04-14 04:37:50 192.168.204.226:49201 <- 89.215.196.42:80 ** GET 89.215.196.42/mod2/5minut1.exe HTTP/1.0 // **
En sonda görüldüğü üzere 5minut1.exe dosyası C2 sunucularından indirilmekte.
Sonuç
Cuckoo ile network paketleri toplanan bir zararlı yazılımın genel itibariyle nasıl bir trafik oluşturduğunu görme imkanımız bulunmakta. Bu işlemide dshell ile oldukça basit komutlar ile wireshar/tshark gibi yazılımların karmaşık komutlarıyla uğraşmadan gerçekleştirebilmekteyiz. Özellikle Dshell’in modül listesinde bulunan xor modülü bazı noktalarda işleri son derece kolaylaştırabilir.