Security/Performance have always been a problem . In this write-up we will build a wordpress web site with consider security, efficiency and cost.
1 – Domain
We will start considering about domain name security. Hackers want to gather information about their target as much as possible. That means we need to keep our domain information secret. So we have to keep domain registerer email address from hacker to be ensure prevention for social engineering attacks. In order to achieve that we can use services of domain companies, like godaddy. Paying $7.99/yearly for your domain you can prevent your personal information from hackers.
2 – VPS Provider DigitalOcean
We’ve choose VPS instead of shared hosting. That will lead to increase cost but we do not want to share our server with someone else. Because when one of the websites that share the same server is compromised, that can effect to our website too. Also we want to be sure about server side configuration. In conclusion, we will be hiring our own VPS.
DigitalOcean is my favourite VPS provider firm. We can easly take snapshot of our virtual machine in order to be sure about backup. Also we can use two factor authentication to ensure one more level security.
We will choose following configuration with CentOs 64bit operating system.
- 1 GB Memory
- 1 Core processor
- 30 GB SSD Disk -which is good for database performance-
- 2 TB Transfer
Before initialize your droplet, you must enable two factor authentication https://cloud.digitalocean.com/settings
When you’ve intialized your droplet, you need to take care of SSH security. First thing you may want to do is disable password authentication in order to prevent ssh brute force attacks. Since we’ve deploy SSH public key into the digitalocean, we can always do public key authentication.
Open /etc/ssh/sshd_config file change do following changes.
# Before PasswordAuthentication yes # After PasswordAuthentication no
That will disable passsword authentication.
3 – Cloudflare for Hide Real IP
Hackers can use DoS attacks against our web site. There is several type of Denial of Services attacks. One of the most common type is L3 Syn Flood attacks. In order to do that type of attack, hackers have to know real ip address of website. We can easily hide our ip address from everyone with using Cloudflare. On the other hand, we can use Compress and Cache CSS/JSS and other services of Cloudflare to increase our system performance without pay a single dollar.
Also you can found steps of setting up cloudflare for godaddy domain http://www.slideshare.net/StanleyTan6/setting-up-cloudflare-for-go-daddy
4 – WordPress requirements
We’ve talk about environmental configuration and options until now. Now we will be talking about tips and tricks about wordpress and server requirements, installation and other software that we will use together.
4.1 Apache and MySQL
You can find well documented guideline for apache + mysql + php installation here.
For efficiency, we need to install only required php packages. Following packages will be enough for wordpress.
[root@host~]# rpm -aq |grep 'php' php-gd-5.3.3-27.el6_5.x86_64 php-mysql-5.3.3-27.el6_5.x86_64 php-common-5.3.3-27.el6_5.x86_64 php-pdo-5.3.3-27.el6_5.x86_64 php-5.3.3-27.el6_5.x86_64
4.2 Cloudflare Real Client Ip Addresses
We may want to analyze our apache log files in certain situations. To get reliable result we need to be sure about ip addresses of log files.
As you know, we are using Cloudflare. We need to do following instructions in order to reach real ip address of clients.
wget https://www.cloudflare.com/static/misc/mod_cloudflare/centos/mod_cloudflare-el6-x86_64.latest.rpm rpm -i mod_cloudflare-el6-x86_64.latest.rpm
Then you need to add following codes to your apache configuration file.
<IfModule mod_cloudflare.c>
CloudFlareRemoteIPHeader CF-Connecting-IP
CloudFlareRemoteIPTrustedProxy 204.93.240.0/24 204.93.177.0/24 199.27.128.0/21 173.245.48.0/20 103.22.200.0/22 141.101.64.0/18 108.162.192.0/18 127.0.0.1/32
#DenyAllButCloudFlare
</IfModule>
PS: I’ve added 127.0.0.1/32 in order to make integrity betweetn apache and varnish. You can add 127.0.0.1/32 subnet to the mod_cloudflare.c file and compile it manually instead of write rules into the apache configuration file.
5 – WordPress Security
5.1 Two Factor Authentication
Once you’ve installed wordpress, you need to install two factor authentication plug-in for wordpress.
Detailed information and installation guideline can be found following url.
https://wordpress.org/plugins/google-authenticator/
Check out live demo : http://mehmetince.net/wp-admin
5.2 File System Security
Changing wordpress php files permissions and groups could be wisely. We need to disable upload theme feature just in case. Because when attackers reach your administrator panel- for instance MITM attacks-, they will immediately try to upload malformed wordpress theme to reach server level access.
chown root:root /var/www/html/wordpress chmod 777 /var/www/html/wordpress/wp-content/upload
We will disable upload feature of wordpress except gallery by executing those linux command. When you need to do main update like install newer version of wordpress, you can easily change root to apache so apache can upload and do changes.
5.3 Do NOT Install Ftp Daemon
Each server side application comes with their security consideration. We do not want to consider about FTP service. We can use SCP in order to upload or download through SSH protocol. We can easily use scp command under the linux/unix system. Also there is number of free application capable for SCP like WinSCP for Windows users.
But wordpress need FTP for plug-in installation or updates by default. We can force wordpress to use HTTP instead of FTP for these kind of purpose by adding following codes to our wp-config.php file.
define('FS_METHOD', 'direct');
5.4 Nulled and Malformed Themes
Do not download and use themes from forums. They could be contains backdoor codes. I’ve experienced lot of similar case. Once you like wordpress theme at themeforest.net just buy it. When you try to find it free or hacked version of theme on internet, you probably see same themes at different web pages but they usually contains backdoor codes!
6 – Apache and MySQL Optimization
Following MySQL configuration is suitable for our application server.
# Optimization key_buffer = 32M query_cache_size = 80M query_cache_limit = 1M query_cache_type = 1 default-storage-engine = myisam skip-innodb
For Apache, default values disabled by adding # at front of the line.
<IfModule prefork.c> #StartServers 8 #MinSpareServers 5 #MaxSpareServers 20 #ServerLimit 256 #MaxClients 256 #MaxRequestsPerChild 4000 StartServers 4 MinSpareServers 8 MaxSpareServers 10 ServerLimit 14 MaxClients 14 MaxRequestsPerChild 2000 </IfModule>
7 – Using Varnish for Speed Up & Content Security Policy
Varnish is a caching HTTP reverse proxy and useful tool for speeding up a server, especially during a times when there is high traffic to a site. But will solve another problem with Varnish too.
Installation and configuration well documented at following web page
http://www.tecmint.com/install-varnish-cache-web-accelerator/
When you’ve done installation of Varnish we need to make few changes on varnish configuration file. First conflict that we will solve is client ip addresses again.
Change your /etc/varnish/default.vcl file with following codes.
IMPORTANT: Following configuration file syntax is for varnish 4.0 version. It will not work with 3.0
vcl 4.0;
# Default backend definition. Set this to point to your content server.
backend default {
.host = "127.0.0.1";
.port = "8080";
}
sub vcl_backend_response {
# Bypass cache for files > 10 MB
if (std.integer(beresp.http.Content-Length, 0) > 10485760) {
set beresp.uncacheable = true;
set beresp.ttl = 120s;
return (deliver);
}
}
sub vcl_recv {
# pipe on weird http methods
if (req.method !~ "^GET|HEAD|PUT|POST|TRACE|OPTIONS|DELETE$") {
return(pipe);
}
### Check for reasons to bypass the cache!
# never cache anything except GET/HEAD
if (req.method != "GET" && req.method != "HEAD") {
return(pass);
}
# don't cache logged-in users or authors
if (req.http.Cookie ~ "wp-postpass_|wordpress_logged_in_|comment_author|PHPSESSID") {
return(pass);
}
# don't cache these special pages
if (req.url ~ "nocache|wp-admin|wp-(comments-post|login|activate|mail)\.php") {
return(pass);
}
# we are behind the cloudflare
unset req.http.X-Forwarded-For;
if (req.http.CF-Connecting-IP) {
set req.http.X-Forwarded-For = req.http.CF-Connecting-IP;
} else {
set req.http.X-Forwarded-For = client.ip;
}
}
Not it’s time to zero information disclosure and Content-Security-Policy. Add following codes to end of the default.vcl files.
# Drop any cookies sent to WordPress.
sub vcl_recv {
if (!(req.url ~ "wp-(login|admin)")) {
unset req.http.cookie;
}
}
# Drop any cookies WordPress tries to send back to the client.
sub vcl_backend_response {
if (!(bereq.http.url ~ "wp-(login|admin)")) {
unset beresp.http.set-cookie;
}
}
sub vcl_deliver {
unset resp.http.Via;
unset resp.http.X-Whatever;
unset resp.http.X-Powered-By;
unset resp.http.X-Varnish;
unset resp.http.Age;
unset resp.http.Server;
set resp.http.X-Frame-Options = "SAMEORIGIN";
set resp.http.X-Xss-Protection = "1; mode=block";
}
We will remove PHP and Web Server version from HTTP Response headers and adding extrea 2 header variables in order to prevent ClickJacking attacks and enabled Reflected XSS protection. You can easily define your javascript, media and images source in here.
Please read following link for other usefull abilities of CSP.
http://www.html5rocks.com/en/tutorials/security/content-security-policy/
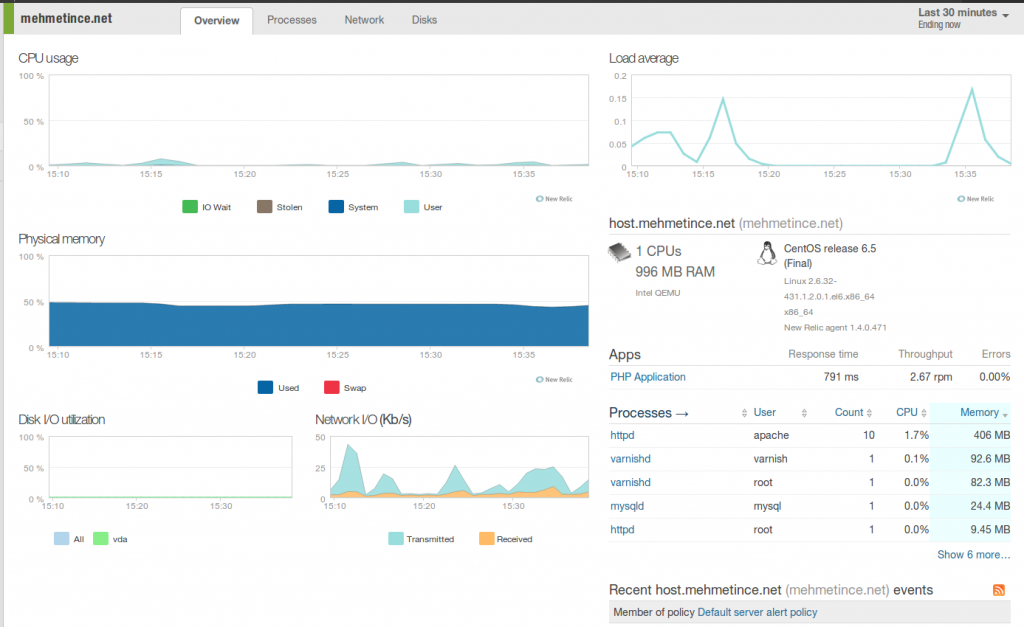
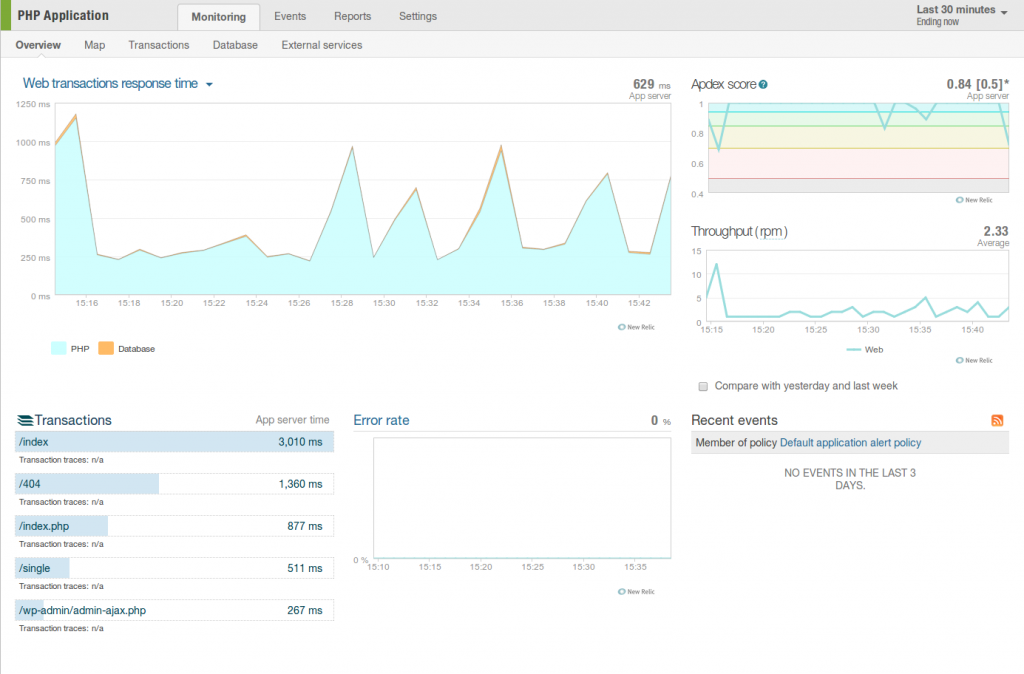
8 – Application and Server Monitoring with Newrelic!
Newrelic offers a performance management solution enabling developers to diagnose and fix application performance problems in real time. You can easily obverse your wordpress application status, execution times, database transaction. Also you can obver I/O, load, CPU and Memory usage of your server too.
Installation and configuration are well documented at newrelic web page you will see once you register.
Newrelic Server Monitoring
Newrelic WordPress Monitoring
Costs of Services
You can use Centos, Apache, MySQL, Varnish, Cloudflare and Varnish for free.